Connectivity considerations for the Hospitality API
Overview
From version 6.10 onwards, Space includes a REST API endpoint designed to handle Apple Wallet key requests for the hospitality industry. This ensures that requests from Apple Wallet-compliant credential managers, located outside the customer premises, are served securely.
In this documentation, the term Hospitality wallet key manager refers to the credential manager software that connects to Space via the Hospitality API to manage the guest's wallet key lifecycle (issuance, revocation, etc.). The Hospitality wallet key manager offers a Hospitality credential manager software that, connected to Space through the Hospitality API, manages the guest wallet key lifecycle (issuance, revocation).
The Apple Wallet key functionality is license-dependent. See Registering and licensing Space for more information.
This section describes a way to establish a secure and reliable integration between the Space software and the credential managers by making direct requests to the customer property's public IP or domain.
Direct requests to customer property's public IP or domain
If this option is not feasible for you, please get in touch with your Salto representative to explore alternative solutions. One such alternative is using a third party wallet key provider, which handles the provisioning of wallet keys that can be used in Space environments.
The direct request process allows the Hospitality wallet key manager to send requests straight to the customer property's public IP address. To enable this, the customer property must apply network-level configurations to accept incoming connections from the Hospitality wallet key manager.
To ensure security, we strongly recommend allowing requests only from the Hospitality wallet key manager's IPs. We will provide the specific IPs from which the Hospitality wallet key manager will make requests to customer properties as needed.
The customer property has the option to decide whether requests will be made to a public IP or to their own domain. If they choose to use a domain, they can use a TLS certificate issued by a Certificate Authority (CA) with a Common Name (CN) matching their domain, and the Hospitality wallet key manager will verify this certificate. Self-signed certificates are also permitted. They can also use CA-verified certificates even if the requests are made to a public IP instead of a domain, but Hospitality wallet key managers cannot verify these certificates.
Important considerations
- The customer property must provide the public IP address and port or domain to which they want the Hospitality wallet key manager to send the requests.
- If the customer property wants to change the public IP, port, or domain to which the Hospitality wallet key manager makes requests, they must notify the appropriate party to ensure proper adjustments in the configuration.
- Make sure you select the Any source option in the configurator under Connection type to ensure the Hospitality wallet key manager can make direct requests to the API.
- The following characters are not allowed when naming rooms and keys: "?", "/", ":", "%", "#", and "". This applies to both the tunnel solution and direct requests. There may also be other special characters that are not permitted.
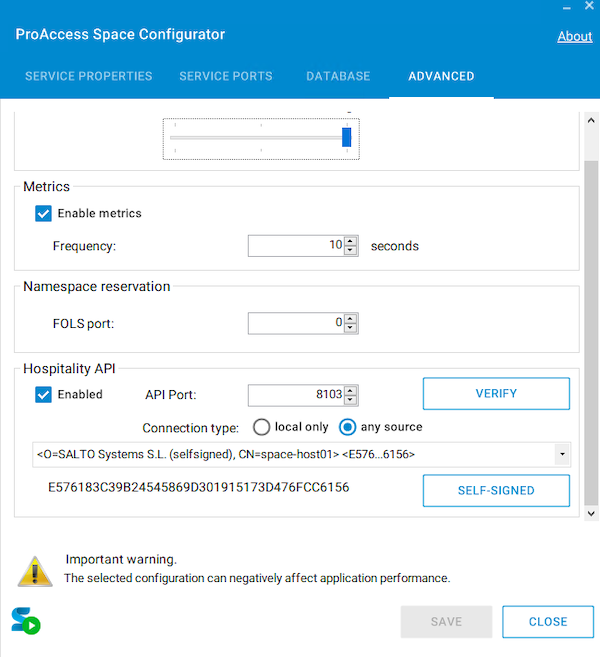 Ensure you select the 'Any source' option in the Space configurator
Ensure you select the 'Any source' option in the Space configurator
 Back
Back